Why Is Compliance Software Important? And How Do I Know If I Need It?
Compliance officers have traditionally spent much of their time manually tracking the data they need to ensure the firm and its employees remain in…
StarCompliance values the security of your business and your data above all else. The STAR platform has been built from the ground up with a focus on security across every product and feature of the application. The STAR platform is hosted in SOC 2 and/or ISO 27001 data centers that provide high availability. As an organization, StarCompliance is ISO 27001, ISO 9001 and SOC2 Type II compliant.

The StarCompliance approach to security is based on a Governance, Risk and Compliance strategy, led and supported from the top down. Our Information Security and Data Protection team ensure that strict policies and procedures are established and implemented in relation to best practice, legislative, regulatory, legal and contractual requirements. These procedures are coupled with the authority to enforce the controls – administrative, technical and physical – which protect our security principles of confidentiality, integrity and availability.
StarCompliance conforms to standards defined by the International Organization for Standardization (ISO) and is certified to:

ISO 27001 – Information Security Management System
Our systematic approach to managing sensitive company information ensures it remains secure. This involves applying robust risk management to our people, processes and IT systems.

ISO 9001 – Quality Management System
Our QMS enables us to identify, measure, control and improve the core business processes that lead to improved business performance.
ISO 27005 is the Risk Management Framework that underpins ISO 9001 and ISO 27001. Risks are identified internally by our Information Security and Data Protection team and externally in our annual, independent, third-party audits.
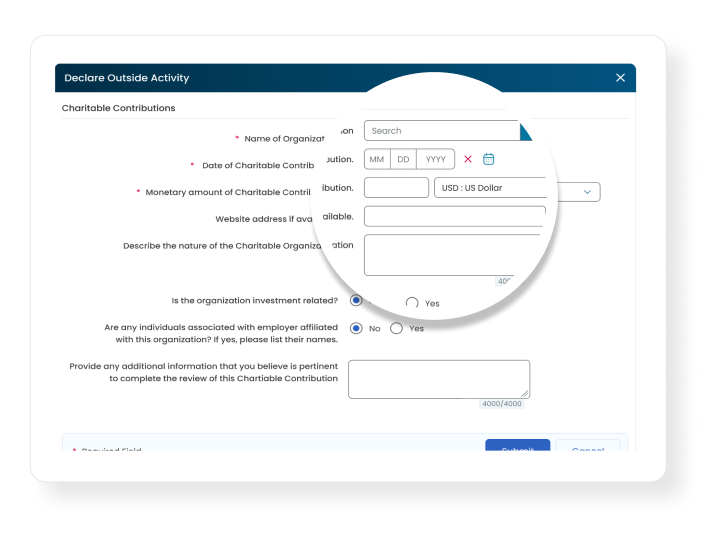
Our compliance program includes:
Star’s advanced implementation and security options ensure your compliance operations are safer and more efficient than ever before.
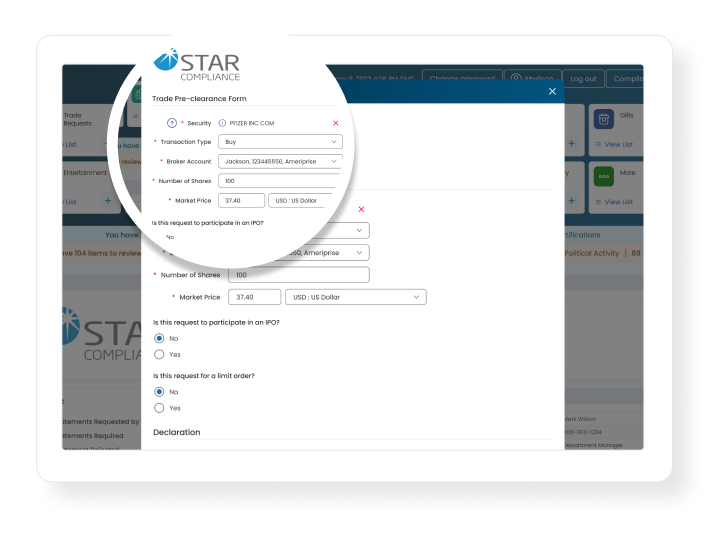
With STAR Mobile, employees pre-clear activity and report transactions on-the-go and Supervisors can review escalated requests from anywhere.
Star offers a range of products, services and vendor solutions that let you monitor and manage an ever-increasing amount of data, enhance and optimize existing data sets, and maintain data integrity.
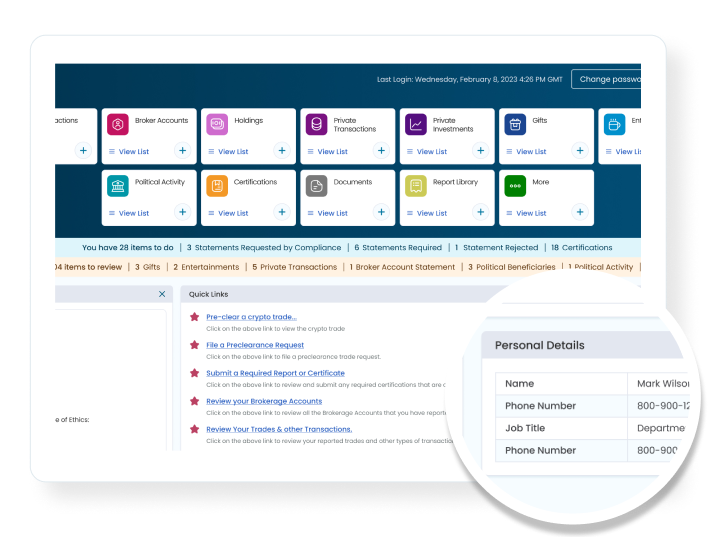
Be proactive, not reactive. Insight Driven Dashboards put actionable intel in front of compliance officers and frontline managers in an interactive format in near-real time.
With Tool Tips & Walkthroughs, the STAR Platform is your compliance software training partner. Get instant support right inside the STAR Platform.
Compliance officers have traditionally spent much of their time manually tracking the data they need to ensure the firm and its employees remain in…

For years, we’ve all paid respect to the disciplines defined by GRC – Governance Risk and Compliance.

For our second annual Crypto & Compliance Survey, we surveyed the marketplace to find out how firms are currently approaching employee crypto-trading compliance and…
